AI in Behavioral Biometrics and User Authentication

In the sphere of cybersecurity, the intricacies of human behavior pose both challenges and opportunities within the authentication field. The shifting paradigms in authentication methodologies reflect a growing realization that the conventional knowledge-based factors, while foundational, are increasingly insufficient in addressing the complexities of human identity.
The traditional triad of authentication factors—something you know, something you have, and something you are—has long been a cornerstone. However, there’s a perceptible shift away from relying solely on the “something you know” category, primarily due to the inherent human limitations in generating and recalling passwords. This transition stems from acknowledging the vulnerabilities of passwords—such as their susceptibility to breaches and the inconvenience they pose to users.
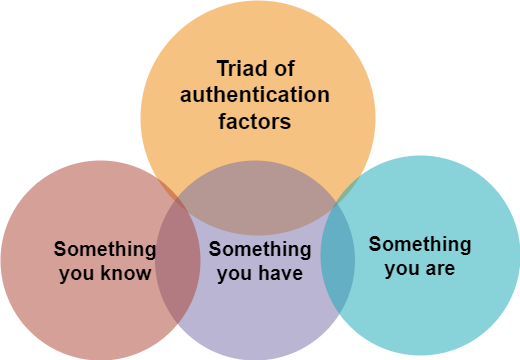
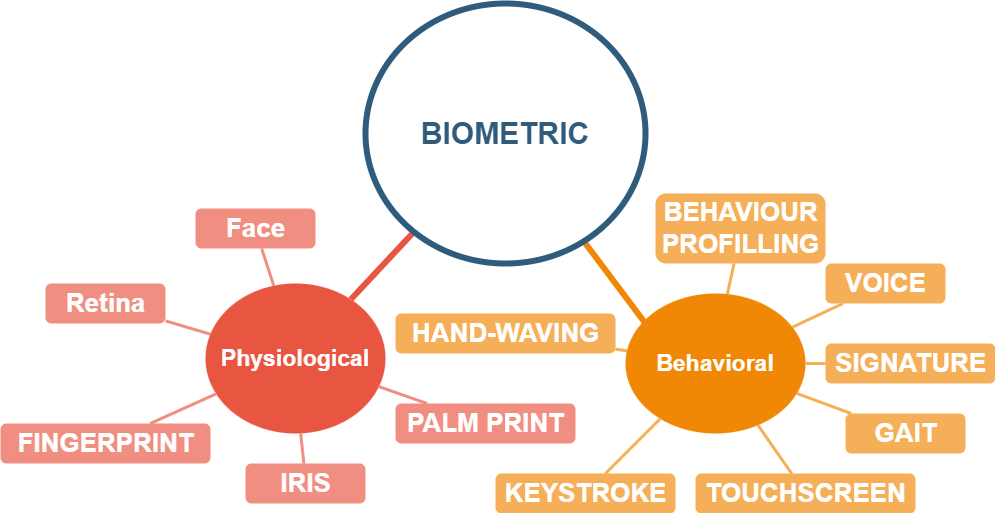
Recognizing these limitations, the focus has expanded toward alternative forms of authentication, namely, “something you have” and “something you are.” The former revolves around possession factors, increasingly centered on mobile devices, S-cards, phone numbers, or email access. Meanwhile, the latter dives into biometrics, extending beyond the traditional fingerprint and face recognition to encompass behavioral biometrics.
Behavioral biometrics present a novel approach, capturing unique behavioral patterns—distinctive to an individual’s muscle memory, habits, or physiology—as a means to validate identity. Unlike static biometrics like fingerprints or facial features, behavioral biometrics are harder to pilfer and offer continuous passive authentication in the background. This continuous monitoring provides a wider dataset for authentication decisions, extending beyond instantaneous measurements to encompass a timeline of activities.
Moreover, behavioral biometrics allow for the detection of changes during an authenticated session, signaling potential compromises in real-time. Early implementations included factors like typing patterns, mouse movements, or IP addresses, valuable for fraud detection but lacking the accuracy required for robust authentication. However, recent advancements focus on more sophisticated behavioral metrics, such as gait analysis, motion sensor data, or on-device biometric sensor data. These factors not only offer stronger authentication accuracy but also enable seamless user experiences across various channels, such as call centers or physical stores.
Implementing such systems, particularly motion authentication, leverages device sensor data to uniquely identify users, even across different devices, ensuring a high level of confidence in user authentication. The integration of these passive authentication techniques vastly improves user experiences without compromising security measures. Furthermore, a layered approach to authentication strategies combining device, contextual, and behavioral signals enhances security. By analyzing data captured before the user engages with a service, authentication policies gain deeper contextual insights, reducing vulnerabilities associated with limited session data.
Best practices in adopting behavioral biometrics include utilizing the phone as a secure authenticator, employing a layered authentication approach, capturing pre-session data, addressing enrollment and data gaps intelligently, and rigorously evaluating system performance with real production data. Behavioral biometrics represent a promising frontier in authentication, providing a compelling blend of heightened security and user convenience. While there’s no one-size-fits-all solution in security, the integration of behavioral biometrics marks a pivotal step towards more sophisticated and reliable authentication methodologies. This evolving landscape urges a shift from binary authentication decisions to dynamic assessments based on a myriad of signals, ultimately paving the way for a more secure digital future.
Technical Underpinnings of AI in Behavioral Biometrics
Data Collection and Feature Extraction
AI algorithms facilitate the extraction of pertinent features from these interactions, transforming raw behavioral data into quantifiable parameters. Behavioral biometrics encompass the capture and analysis of diverse user interactions such as:
Keystroke Dynamics. Capture and analysis of the timing, duration, and pressure of key presses while typing. This includes the time intervals between successive keystrokes, key hold durations, and the specific sequence of key combinations.
Mouse Movements. Monitoring and recording the trajectory, speed, acceleration, and patterns of mouse movements across the screen. This involves tracking cursor movements, clicks, scrolling behavior, and dwell times on different elements.
Typing Cadence. Analysis of typing rhythm and style, including variations in typing speed, pauses between words or sentences, typing errors, and the overall fluency of typing.
Gesture Patterns. Observing and interpreting gestures made on touch-sensitive devices, such as swipe patterns, pinch-to-zoom actions, or specific movement sequences executed on touchscreens.
Touchscreen Pressure. Capturing and analyzing variations in pressure applied to touchscreen devices, which can indicate unique patterns in how users interact with the screen.
Feature Extraction Techniques
Time-Based Features. Extracting temporal characteristics such as inter-key press intervals, duration of mouse movements, time taken for specific gestures, and intervals between touch interactions.
Statistical Parameters. Calculating statistical measures like mean, median, standard deviation, variance, and skewness of behavioral data, providing insights into the distribution and variability of user interactions.
Frequency Domain Analysis. Utilizing techniques like Fast Fourier Transform (FFT) to analyze behavioral signals in the frequency domain. This method helps identify periodic patterns or specific frequencies present in user interactions.
Pattern Recognition. Employing pattern recognition algorithms to detect and extract unique patterns within the data. This involves identifying clusters or sequences in keystrokes, mouse movements, or gesture patterns.
Machine Learning-Based Features. Leveraging machine learning models to automatically extract relevant features. For instance, using deep learning architectures to learn representations from raw data through neural networks, extracting abstract features that signify distinct behavioral traits.
Machine Learning Models
Sophisticated machine learning models, including neural network architectures like Long Short-Term Memory (LSTM) networks or traditional classifiers such as Support Vector Machines (SVM), learn and identify intricate patterns within the extracted behavioral features. These models undergo training using labeled datasets containing examples of authentic user behavior.
Labeled Datasets. Training machine learning models for behavioral biometrics requires labeled datasets containing examples of genuine user behavior. These datasets encompass diverse behavioral interactions, each labeled with the corresponding user identity or behavior category. For instance, keystroke dynamics labeled as ‘authentic user’ or ‘anomalous behavior’ for user authentication purposes.
Feature Engineering and Preprocessing. Before training, feature engineering techniques are applied to extract relevant features from raw behavioral data. Preprocessing steps may involve normalization, scaling, or dimensionality reduction to ensure uniformity and optimize the model’s performance.
Model Training and Evaluation. During training, the machine learning models learn to map the extracted behavioral features to corresponding user identities or behavior categories. Training involves adjusting model parameters to minimize classification errors or maximize predictive accuracy. Models are evaluated using metrics such as accuracy, precision, recall, and F1-score on validation or test datasets to assess their performance.
Continuous Monitoring and Real-time Analysis
AI-driven behavioral biometrics facilitate continuous monitoring and real-time analysis of user behavior. This real-time scrutiny enables instant anomaly detection, enabling swift responses to potential security threats or unauthorized access attempts.
Case Studies Demonstrating AI’s Efficacy in Anomaly Detection
Case Study 1. Financial Sector Fraud Detection
A recent study conducted by a leading financial institution leveraged AI-driven behavioral biometrics to detect fraudulent activities. The system monitored user behavior during financial transactions, analyzing subtle variations in typing speed, mouse movements, and navigation patterns. The AI model successfully flagged anomalous behaviors, leading to the prevention of numerous fraudulent transactions.
Case Study 2. Insider Threat Detection in Corporate Environments
In a corporate setting, an AI-powered behavioral biometric system monitored employee activities across digital platforms. By analyzing email communication patterns, file access timestamps, and device usage habits, the system identified anomalous behaviors indicative of potential insider threats. Prompt intervention prevented data breaches and safeguarded sensitive corporate information.
AI’s integration into Behavioral Biometrics heralds a new era in user authentication and security. The amalgamation of advanced algorithms and machine learning techniques empowers systems to authenticate users based on nuanced behavioral nuances, significantly fortifying security measures. With ongoing research and technological advancements, the realm of AI-driven behavioral biometrics promises to continue revolutionizing user authentication and cybersecurity protocols.










