AI Techniques in Cybersecurity

In cybersecurity sphere, a multitude of cutting-edge AI algorithms and models are at the forefront, transforming threat detection and mitigation, helping to detect and cut them off. These article includes the latest AI algorithms and models commonly used in cybersecurity.
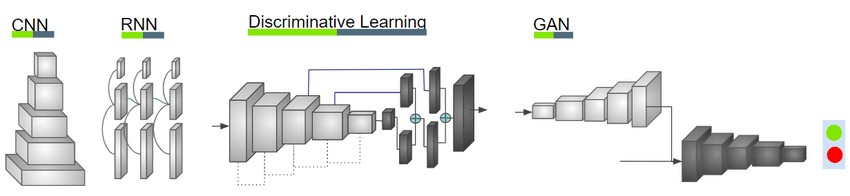
Convolutional Neural Networks (CNNs)
Originally popular in image processing, CNNs are increasingly applied in cybersecurity for analyzing sequences of network packets. They excel in detecting anomalies within network traffic patterns, identifying potential threats such as malware or intrusions. In cybersecurity, CNNs represent a potent tool in analyzing and deciphering network traffic patterns, identifying potential threats, and contributing to stronger defense against changing cyberattacks. As progress in AI and cybersecurity meets, usage of CNNs’ capabilities holds promise in fortifying digital infrastructures against increasingly sophisticated threats.
How CNNs are Used as an AI Algorithm in Cybersecurity
Pattern Recognition in Network Traffic. CNNs is excellent in analyzing sequences of data, making them particularly useful in processing network traffic patterns. In cybersecurity, they are expert at understanding the structure of packet data, allowing them to recognize normal network behaviors from potentially harmful activities. By accepting a stream of network packets, CNNs can identify anomalies and suspicious patterns that may indicate various cyber threats, such as intrusions, malware, or abnormal traffic flows.
Feature Extraction and Hierarchical Learning. One of the key strengths of CNNs lies in their ability to automatically extract relevant features from raw data. In the context of network traffic analysis, CNNs can automatically learn and extract hierarchical features, identifying intricate patterns within different layers of the network packets. This hierarchical learning enables CNNs to differ subtle anomalies or deviations from regular network behaviors.
Unsupervised Anomaly Detection. CNNs are used for unsupervised anomaly detection, where they learn the normal patterns present in network traffic without the need for obvious labeling of anomalous data. Through this approach, CNNs can detect deviations from learned normal behavior, signaling potential security threats without prior knowledge of specific attack signatures.
Real-world use cases of CNNs in cybersecurity
Malware Detection. CNNs have been applied to analyze code sequences and binary files to detect patterns indicative of malicious software. They can identify signatures or behavioral patterns associated with malware, aiding in early detection and prevention of cyber threats.
Intrusion Detection Systems (IDS). CNNs are used in network traffic analysis for intrusion detection. They analyze network packet data to recognize abnormal traffic patterns, anomalies, or suspicious activities that might signify unauthorized access attempts or intrusions into a network.
Phishing Detection. CNNs are employed to analyze email content, URLs, and website structures to detect phishing attempts. They can identify visual and textual cues within emails or web pages that resemble known phishing schemes, assisting in identifying and preventing phishing attacks.
Network Anomaly Detection. CNNs analyze network logs and traffic flows to detect anomalies that might indicate potential security breaches. They are expert at recognizing irregularities in network behavior, such as distributed denial-of-service (DDoS) attacks or unusual access patterns, aiding in early threat detection.
IoT Security. CNNs are used in securing Internet of Things (IoT) devices by analyzing data streams generated by IoT sensors. They detect anomalous patterns in device behavior or communication, helping to identify potential vulnerabilities or compromised devices in IoT networks.
Deep Packet Inspection. CNNs are employed in deep packet inspection to analyze and classify packets within network traffic. They can extract features from packet headers or payloads, enabling identification and filtering of suspicious or harmful traffic.
Example of CNN-based approach
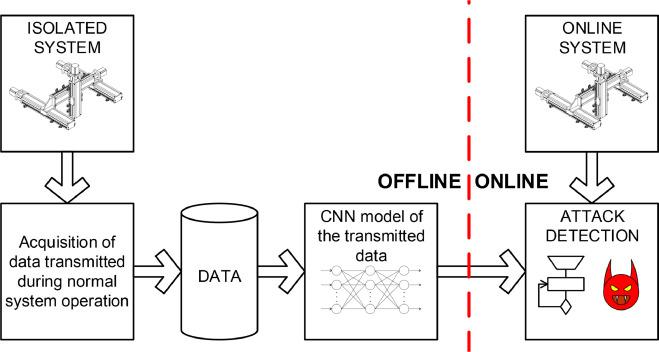
The article “Maritime Cyber-Attacks Detection Based on a CNNs” discusses the increasing vulnerability of maritime transportation systems to cyber threats due to their integration into cyberspace. It highlights the rising risk of cyber-attacks, including altering vessel courses and causing port congestion, emphasizing a 900% increase in such incidents over the last time. To address these challenges, the paper proposes the use of a Convolutional Neural Network (CNN) for detecting anomalies in maritime communications.
Article addresses the susceptibility of maritime vessels to cyber-attacks due to accessibility, underscoring the potential risks that cyber-attacks pose, including criminal and terrorist acts.
To protect maritime transportation data, the article introduces a CNN-based approach aimed at detecting anomalies in received data and extracting features from GNSS data to identify the sources of anomalous data. It emphasizes the system’s goal to recognize ship types and associated cyber-attacks, employing accurate measurement methods for comparisons and predictions.
The paper also discusses the significance of maritime cybersecurity, focusing on cyber-attack detection and anomaly-based statistical measurements using augmented GNSS. It outlines the system model, CNN architecture, detection of anomalous data, and encryption approaches to secure maritime communications. Furthermore, it introduces a blockchain strategy for data communication security between maritime IoT devices and emphasizes the importance of anomaly detectors in identifying abnormal behavior within networks.
Effectiveness of CNNs in cybersecurity by usage their ability to analyze complex data structures, recognize patterns, and detect anomalies is pretty high. However, the effectiveness of CNNs depends on the quality and diversity of data available for training and the specific architecture tailored to the cybersecurity task at hand.
While CNNs offer significant potential in cybersecurity, their implementation faces challenges. CNNs require substantial computational resources, and training models for cybersecurity applications demands large amounts of labeled data, which may be short in the cybersecurity sphere.
The future of CNNs in cybersecurity lies in increasing their interpretability, efficiency, and scalability. Researchers aim to develop CNN-based models that not only detect anomalies but also provide explanations for their detections, enabling cybersecurity professionals to comprehend and act upon the identified threats effectively.
Recurrent Neural Networks (RNNs)
RNNs have emerged as a powerful AI algorithm in cybersecurity especially in analyzing sequential data and detecting anomalies within complex network behaviors. They can identify anomalies in sequences of network activities, aiding in detecting unusual behaviors and potential cyber threats.
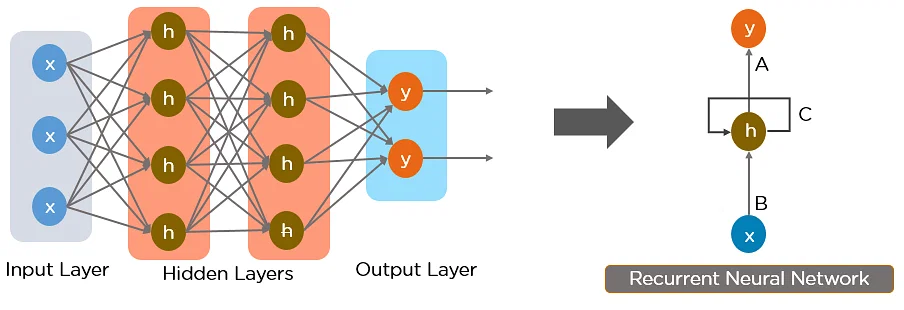
How RNNs are Utilized as an AI Algorithm in Cybersecurity
Understanding Sequential Data. RNNs are uniquely suited for processing sequential data, making them invaluable in cybersecurity for analyzing time-series data, network traffic logs, or system logs. Unlike traditional neural networks, RNNs possess memory cells that save information about previous inputs, enabling them to capture temporal dependencies and patterns within sequences of data.
Anomaly Detection in Temporal Data. In cybersecurity, RNNs are employed to identify anomalies and irregularities within sequences of network activities. By learning the temporal relationships between successive data points, RNNs can discern normal network behaviors from abnormal or suspicious activities. For instance, RNNs can recognize deviations from usual traffic patterns or detect unusual sequences of system commands, flagging potential security breaches or malicious activities.
Long-Term Dependencies and Contextual Understanding. One of the key advantages of RNNs is their ability to capture long-term dependencies in sequential data. In cybersecurity, this allows RNNs to maintain context across multiple time steps, recognizing complex patterns that might indicate security threats. RNNs can remember crucial information over extended periods, aiding in the identification of subtle anomalies that traditional methods might overlook.
Real-world use cases of RNNs in cybersecurity
Recurrent Neural Networks have found practical applications in various cybersecurity domains due to their capability to process sequential data and capture temporal dependencies.
Network Intrusion Detection. RNNs have been employed to analyze network traffic logs and sequences for detecting anomalies or suspicious patterns. They can recognize deviations from normal behavior, such as unusual sequences of commands or data packets, indicating potential cyber threats like intrusions or malware activities.
Malware Detection. RNNs are used to analyze sequences of code or binary data to identify patterns indicative of malware. They can learn sequences of commands or code structures that distinguish between benign and malicious software, aiding in malware detection and prevention.
Predictive Threat Analysis. RNNs have been applied for predictive analysis in cybersecurity. By analyzing historical attack patterns and sequences of cyber incidents, RNNs can forecast potential threats or cyber attacks, allowing security teams to prepare and implement proactive measures.
Behavioral Analysis. RNNs are used for analyzing user behavior and activity logs within systems. They can learn patterns of normal behavior and detect deviations that might suggest unauthorized access or suspicious activities, facilitating user authentication and access control.
Phishing Detection. RNNs have been employed to analyze patterns in emails or website content to detect phishing attempts. By learning from sequences of text or HTML structures, RNNs can identify characteristics typical of phishing emails or deceptive websites.
Predictive Maintenance for Cybersecurity Systems. RNNs are used for predictive maintenance of cybersecurity systems. They can analyze sequences of system logs or sensor data to predict potential failures or vulnerabilities in security infrastructure, enabling proactive maintenance and fortification.
Research: Recurrent neural networks for Cybersecurity use-cases research
These real-world applications demonstrate the practical usage of Recurrent Neural Networks in various aspects of cybersecurity, increasing their ability to handle sequential data and extract meaningful patterns or anomalies crucial for threat detection and mitigation.
Despite their effectiveness, RNNs come with certain challenges in cybersecurity applications. Long-range dependencies can sometimes lead to vanishing or exploding gradients during training, affecting the model’s ability to learn effectively from long sequences of data. Additionally, RNNs may struggle with processing extremely large datasets or real-time streaming data due to computational constraints.
RNNs development in cybersecurity involves addressing their limitations, improving their ability to handle large-scale datasets, and optimizing their efficiency for real-time processing. Innovations in model architectures, such as Long Short-Term Memory (LSTM) networks and Gated Recurrent Units (GRUs), aim to enhance RNNs’ capabilities in handling sequential data more effectively.
As cybersecurity threats continue to improve, using RNNs’ ability to comprehend temporal dependencies holds significant promise in fortifying digital defenses.
How LSTMs are Used as an AI Algorithm in Cybersecurity
Long Short Term Memory Networks – specialized type of Recurrent Neural Network (RNN) designed to overcome the limitations of traditional RNNs in handling long-range dependencies in sequential data. In cybersecurity, LSTMs are used for anomaly detection in network traffic, recognizing unusual patterns that might indicate security breaches, fortifying digital defenses.
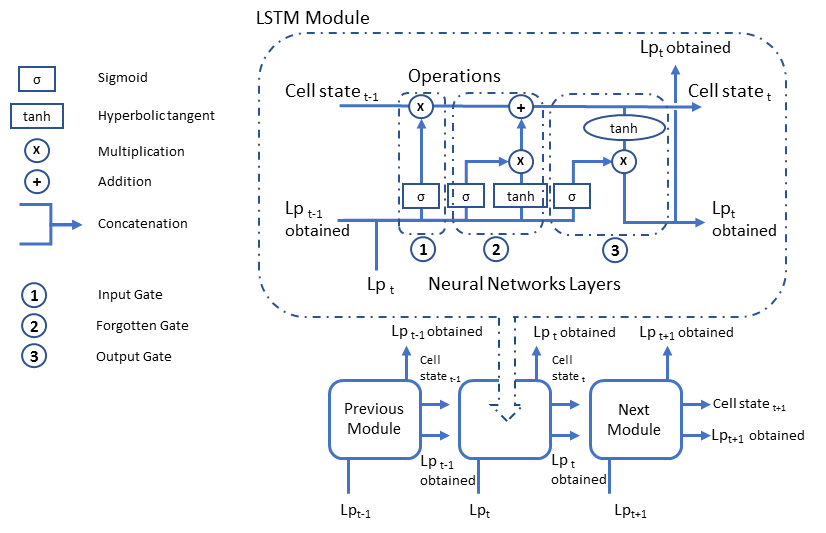
Capturing Long-Term Dependencies. LSTMs excel in capturing and retaining information over extended sequences, making them highly effective in handling time-series data prevalent in cybersecurity. Unlike traditional RNNs, LSTMs have a unique architecture with memory cells and gates that enable them to remember relevant information for longer durations, facilitating the understanding of long-term dependencies in sequential data.
Anomaly Detection in Network Traffic. One of the primary applications of LSTMs in cybersecurity is anomaly detection within network traffic. By analyzing sequences of network activities, LSTMs can learn the normal behavior of network traffic and identify deviations or irregularities that might indicate potential security threats. They can recognize subtle patterns, such as abnormal data transmissions or unusual access attempts, signaling possible cyber attacks or breaches.
Feature Learning and Adaptability. LSTMs are adept at learning complex features and patterns from raw sequential data. In cybersecurity, they autonomously extract informative features from network logs, system events, or other time-series data sources. This adaptability allows LSTMs to continuously evolve and adapt to new attack patterns, enhancing their ability to detect emerging threats in dynamic cyber landscapes.
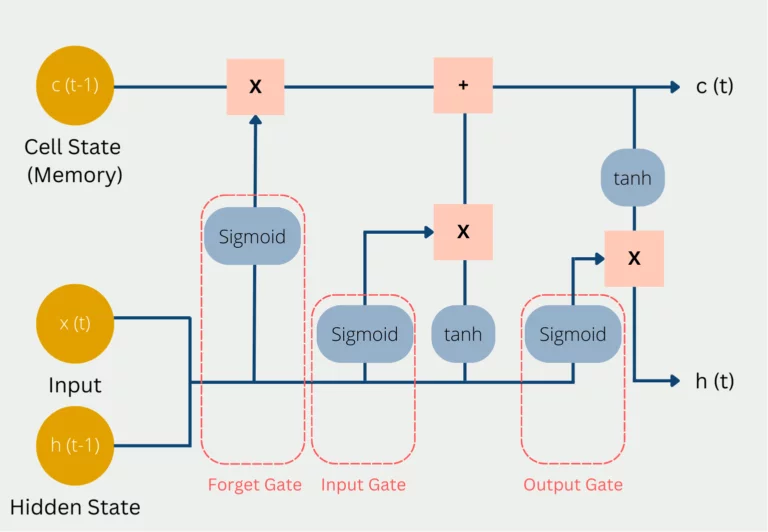
LSTM Architecture
Real-world use cases of LSTMs in cybersecurity
Long Short-Term Memory (LSTM) networks, a type of recurrent neural network (RNN), have found practical applications in cybersecurity due to their ability to handle sequential data effectively.
Fraud Detection in Financial Transactions. LSTMs are used to analyze sequences of financial transaction data to detect anomalies or fraudulent behavior. They can learn patterns in transaction sequences that deviate from normal user behavior.
Log Analysis and Anomaly Detection. Long Short-Term Memory are applied in analyzing logs generated by various systems to detect abnormal patterns or suspicious activities. They can learn the temporal dependencies and sequences in log entries to identify anomalies that might indicate security breaches or system malfunctions.
Network Intrusion Detection. Neural network have been used to detect anomalous patterns in network traffic data. By analyzing sequences of network packets and their temporal relationships, LSTMs can identify suspicious activities or potential intrusions.
Threat Intelligence and Predictive Analysis. LSTMs can analyze historical data to predict potential cybersecurity threats. By learning from past incidents and patterns, they can forecast possible future attacks or vulnerabilities.
Malware Detection. Long Short-Term Memory are employed to analyze the behavior of executable files and detect malicious software. By examining sequences of system calls or API invocations generated by software, LSTMs can identify patterns indicative of malware behavior.
Phishing Detection. Analyzing the sequence of user interactions and behaviors in online activities, such as email correspondence or website navigation, LSTMs can identify patterns associated with phishing attacks or fraudulent activities.
User Behavior Analysis. LSTMs can be used to model and analyze the sequence of actions or behaviors of users on networks or systems. By learning patterns of normal behavior, they can identify deviations that might signal security threats, such as insider threats or unauthorized access.
Research: LSTM Deep Learning Method for Intrusion Detection in Network Security
In these applications, LSTMs excel in handling sequential and time-series data, providing an advantage over traditional machine learning models. They can capture long-term dependencies, learn from temporal relationships, and effectively model complex patterns in cybersecurity data to improve threat detection and mitigate security risks.
Due to their capability to process sequential data in real-time, LSTMs hold promise in predicting and responding to cyber threats as they unfold. By learning from historical data patterns, LSTMs can forecast potential security incidents, enabling proactive measures to mitigate risks and respond swiftly to evolving cyber threats.
Challenges associated with deploying LSTMs in cybersecurity include the need for substantial computational resources and labeled data for training robust models. Future advancements aim to address these challenges by optimizing model architectures, improving efficiency, and developing techniques to handle large-scale datasets more effectively.
As advancements continue, harnessing the potential of LSTMs holds significant promise in enhancing cybersecurity practices and mitigating risks in an ever-evolving digital environment.
Generative Adversarial Networks
GANs have gained attention for their ability to simulate and generate synthetic data. It is a class of AI models comprising two neural networks – the generator and the discriminator – engaged in a competitive game. While primarily known for generating synthetic data, GANs are increasingly being explored in cybersecurity for their potential to simulate attacks, enhance defenses, and augment security measures.
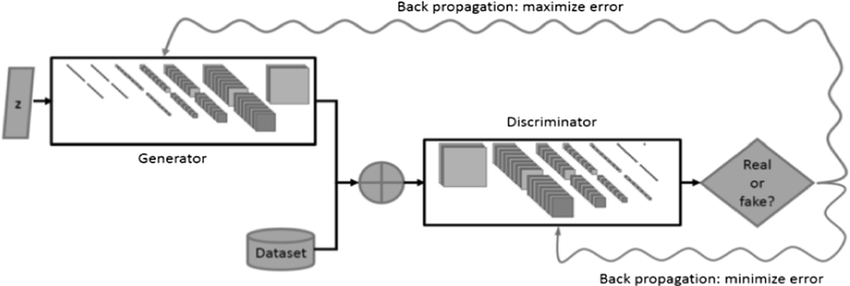
GAN Architecture
How GANs are Used as an AI Algorithm in Cybersecurity
Adversarial Training and Simulation. In cybersecurity, GANs can simulate adversarial attacks, creating synthetic data that mimic potential threats. The generator within GANs is trained to generate data samples that are indistinguishable from real data, while the discriminator aims to distinguish between real and synthetic data. This adversarial training enables GANs to produce realistic attack scenarios, aiding in fortifying defenses against these simulated threats.
Generating Synthetic Data for Testing. One of the key applications of GANs in cybersecurity is generating synthetic data for testing and evaluating security systems. GANs can create realistic datasets representing different cyber threats, enabling security practitioners to assess the resilience of their systems against various attack scenarios without risking exposure to real threats.
Augmenting Security Measures. By mimicking potential attack patterns, GANs help in identifying vulnerabilities and weaknesses in cybersecurity defenses. Security professionals can use GAN-generated data to proactively assess and improve the robustness of intrusion detection systems, anomaly detection algorithms, and other security mechanisms.
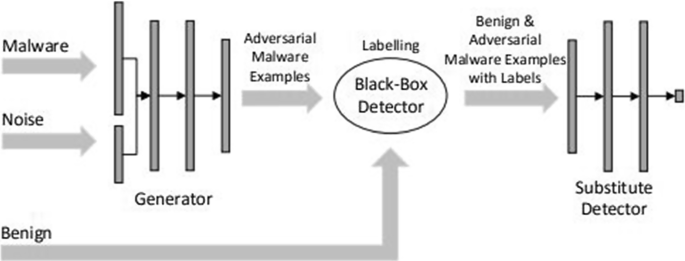
Real-world use cases of GANs in cybersecurity
Generative Adversarial Networks have shown promise in various applications within cybersecurity due to their ability to generate synthetic data that resembles real data.
Network Security Testing. GANs can generate synthetic network traffic that resembles real-world traffic. Security analysts and researchers can use this synthetic data to simulate and test security measures, evaluate the effectiveness of intrusion detection systems, or assess vulnerabilities in network architectures without risking real data or systems.
Data Augmentation. Can generate synthetic data to augment existing datasets. In cybersecurity, this can be beneficial for training models in scenarios where labeled data is scarce, such as in malware detection or intrusion detection systems. By creating additional synthetic data, GANs help improve the robustness and performance of machine learning models.
Anomaly Detection. Generative Adversarial Networks can assist in detecting anomalies by learning the normal patterns within a dataset and generating synthetic samples that deviate from these patterns. By comparing real data with generated data, GANs can help identify outliers or anomalies that might indicate potential security threats or irregularities in network traffic, system logs, or user behavior.
Adversarial Training. GANs can be employed to train cybersecurity models against adversarial attacks. For instance, in intrusion detection systems or malware classifiers, GANs can generate adversarial samples to evaluate the robustness of these models against crafted attacks. This helps in improving the resilience of cybersecurity systems against sophisticated attacks.
Privacy Protection. Can be used to generate privacy-preserving synthetic data that retains the statistical properties of sensitive datasets while ensuring individual privacy. This is particularly relevant in scenarios involving sharing or publishing datasets for research or analysis without disclosing sensitive information.
Password and Key Generation. Generative Adversarial Networks can be used to generate passwords or encryption keys that exhibit complexity and randomness. This can aid in strengthening security measures by creating strong and diverse authentication credentials.
Counterfeit Detection. GANs can help detect counterfeit digital assets or documents by generating synthetic data that resembles legitimate items. By comparing real and generated data, discrepancies can be identified, assisting in the identification of fraudulent or counterfeit materials.
The deployment of GANs in cybersecurity faces challenges, including the ethical implications of creating realistic synthetic attack scenarios. Ensuring that GAN-generated data is used responsibly and ethically, avoiding unintentional harm or misuse, is a critical consideration. Additionally, GANs require careful calibration and validation to produce accurate and representative synthetic data.
The future of GANs in cybersecurity involves refining their ability to generate diverse and complex attack scenarios. Researchers are exploring novel architectures and training techniques to enhance GANs’ capabilities in mimicking sophisticated attacks and further improving their usefulness in cybersecurity testing and training. Using GANs’ adversarial training capabilities offers opportunities to fortify defenses, identify vulnerabilities, and bolster the resilience of cybersecurity measures in an increasingly complex digital ecosystem. However, ethical considerations and responsible usage remain paramount in harnessing the potential of GANs in cybersecurity practices.
These algorithms demonstrate significant promise in detecting anomalies, fortifying defenses, and simulating potential threats. While they offer immense potential, challenges like computational demands, data requirements, ethical considerations, and the need for responsible deployment remain crucial. The future of cybersecurity lies in enhancing these algorithms’ interpretability, efficiency, and scalability while ensuring ethical use to effectively safeguard digital infrastructures against evolving cyber threats.










