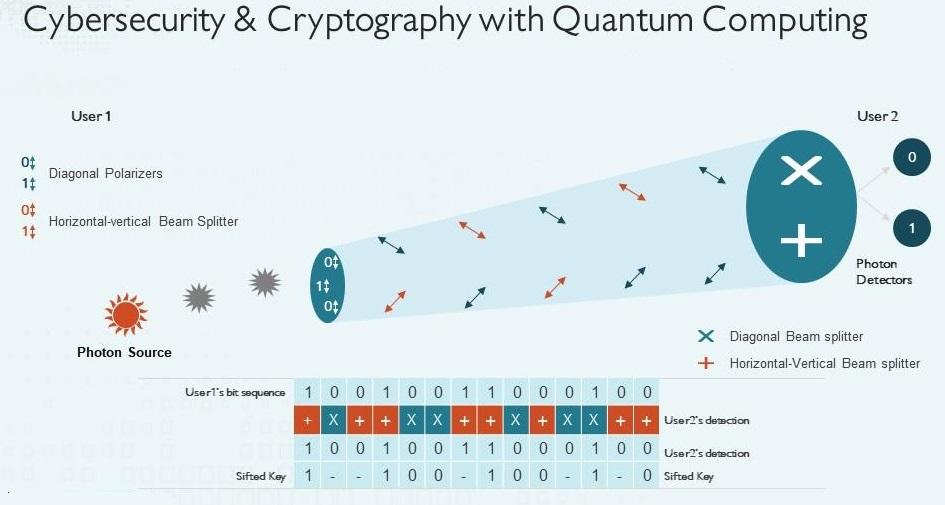
Quantum Computing and AI in Cybersecurity

Artificial Intelligence and Quantum Computing stand as formidable forces shaping the technological field. AI harnesses algorithms to process vast data quantities, enabling systems to learn patterns or rules embedded within these algorithms.
On the other hand, quantum computing leverages principles of quantum mechanics to execute simultaneous computations, surpassing the speed and efficiency of conventional computers. The immense power of quantum computing poses a theoretical threat, as a single quantum computer could potentially surpass the combined capabilities of all current supercomputers. The mastery of quantum computing by a state could theoretically lead to unprecedented hacking capabilities, breaching networks, databases, and critical infrastructure systems with minimal resistance.
The convergence of AI and Quantum Computing raises profound concerns regarding national security. Defending against these technologies poses an exceptionally complex challenge, amplifying the potential for them to become significant threats in the realm of national security.
AI – Future of Cybersecuriry
AI possesses remarkable problem-solving, planning, research, and speech recognition skills. Its intricate algorithms have shattered expectations, raising concerns among experts about its potential enormity and potency. Surpassing human capabilities, AI systems showcased exceptional efficiency and prowess in various domains, with tech giants like IBM and Microsoft employing AI in their innovative platforms such as IBM’s Watson and Microsoft’s Azure Machine Learning Program. These systems excel in rapid computing and profound research, showcasing AI’s potential for immense benefits and innovation.
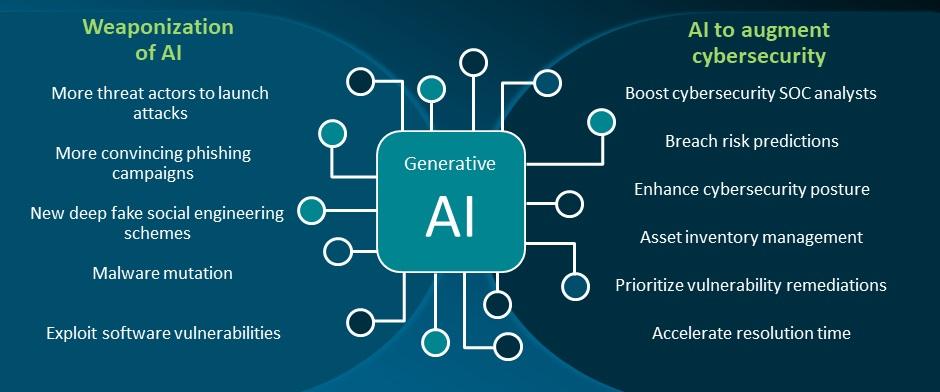
However, AI’s strengths also underscore its vulnerabilities, particularly in the realm of cyberwarfare. The integration of AI into global systems introduces substantial risks, including cyberattacks on AI databases, integration of AI into conventional military operations, and heightened threats to national security. Current AI systems face data breaches due to unsecured centralized servers, making them easy targets for hackers to exploit valuable information, posing threats to individuals, businesses, and governments.
Moreover, the incorporation of AI in conventional warfare raises concerns about autonomous weapons systems capable of sophisticated problem-solving and decision-making akin to humans. This prospect has led to debates urging international bodies, like the United Nations, to consider banning lethal AI autonomous weapons due to the potential for conflicts on an unprecedented scale, faster than human comprehension.
The vulnerability of AI databases to cyberattacks poses substantial national security threats, including severe damage to critical infrastructure and widespread human casualties. The complexities of integrating AI into the cyber domain have begun to impact international relations and will likely continue to do so. Despite the associated dangers and challenges, the advantages and capabilities AI offers continue to drive further research and innovation in the field.
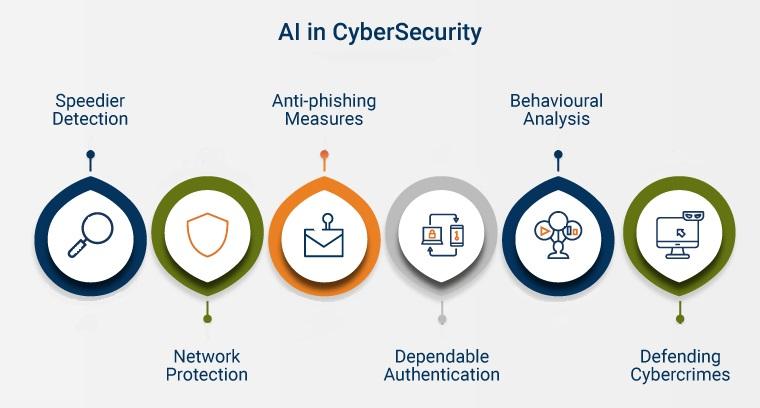
Quantum Computing’s Race and Cybersecurity
Quantum mechanics, though aged in the information age, has garnered significant attention in cyber warfare discussions owing to its potential when a quantum computer materializes. Evolving since the early twentieth century, quantum computing and its applications have grown increasingly intricate with advancing technology.
A quantum computer, as defined by the National Academy of Sciences, operates using qubits, distinct from classical computers that rely on binary digits or bits. Qubits, unlike classical bits, exist in both zero and one states simultaneously, leveraging superposition to perform computations much faster. These systems embody unique quantum properties – superposition, measurement, collapse, entanglement, and coherence—unveiled through decades of scientific exploration.
While quantum computers offer immense potential, they grapple with self-imposed constraints. Four key constraints limit their capabilities: the inability to interact among entangled qubits, the no-cloning principle, susceptibility to external environmental interference, and challenges in accurately measuring particles in a quantum state. Despite these limitations, nations worldwide are vigorously pursuing the development of large-scale, operational quantum computers due to their unparalleled potential.
The advancement of quantum technology unfolds slowly, with many potential dangers still unknown. However, it’s understood that once operational, quantum computers will possess the ability to breach public key cryptosystems, potentially reshaping warfare. Cybersecurity and industry leaders express concerns about the impending mainstream integration of quantum computers. The worry stems from the potential obsolescence of current public key encryption algorithms, particularly RSA (Rivest Shamir Adleman), driven by the implications of Shor’s Algorithm. This revolutionary algorithm, if utilized by sufficiently powerful quantum computers, could render contemporary public key encryption algorithms ineffective almost instantly. Shor’s Algorithm possesses the capability to swiftly compute the factors of colossal numbers, a fundamental operation underlying modern public key encryption, at speeds far surpassing those achievable by current computing devices.
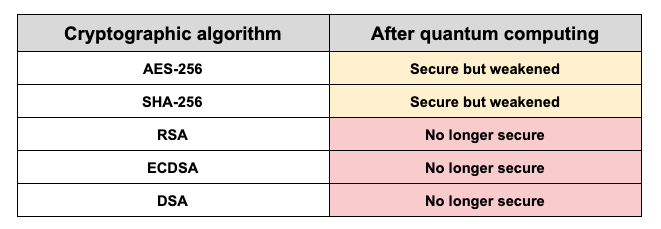
When attempting to crack asymmetric encryption like RSA using classical computers, the primary challenge involves guessing the factors of these extraordinarily large integers. This endeavor proves exceedingly time-consuming when relying on conventional computing methods. However, leveraging quantum properties drastically diminishes the time required for such calculations, reducing the lengthy computations that could take millions of years on traditional computers to mere minutes for a quantum computer.
The race to develop a functional quantum computer is likened to a technological arms race, as nations strive for dominance. Scientists warn that the creation of large-scale quantum computers could dismantle current encryption systems, granting significant power to those in possession. This technology could disrupt military, government, and economic infrastructures, reshaping global politics and security.
The competition to lead in quantum computing stands as a crucial pursuit, mirroring historical arms races, as it could dictate future geopolitical dominance or create mutual assured destruction if mishandled or accessed by adversarial nations.
Developing Quantum-Resistant Cryptography
Researchers are actively engaged in crafting public-key algorithms resilient against decryption by quantum computers. These efforts aim to safeguard certificate authorities, digital signatures, and encrypted messages, ensuring continued trust in these security measures.
The U.S. National Institute of Standards and Technology (NIST) is spearheading the evaluation of 69 potential “post–quantum cryptography” methods. Subsequently, NIST unveiled these 69 candidate algorithms, encouraging cryptographers to scrutinize and attempt to crack them. Employing an open and transparent approach, NIST conducted multiple evaluation rounds to progressively narrow down the pool of candidate algorithms.
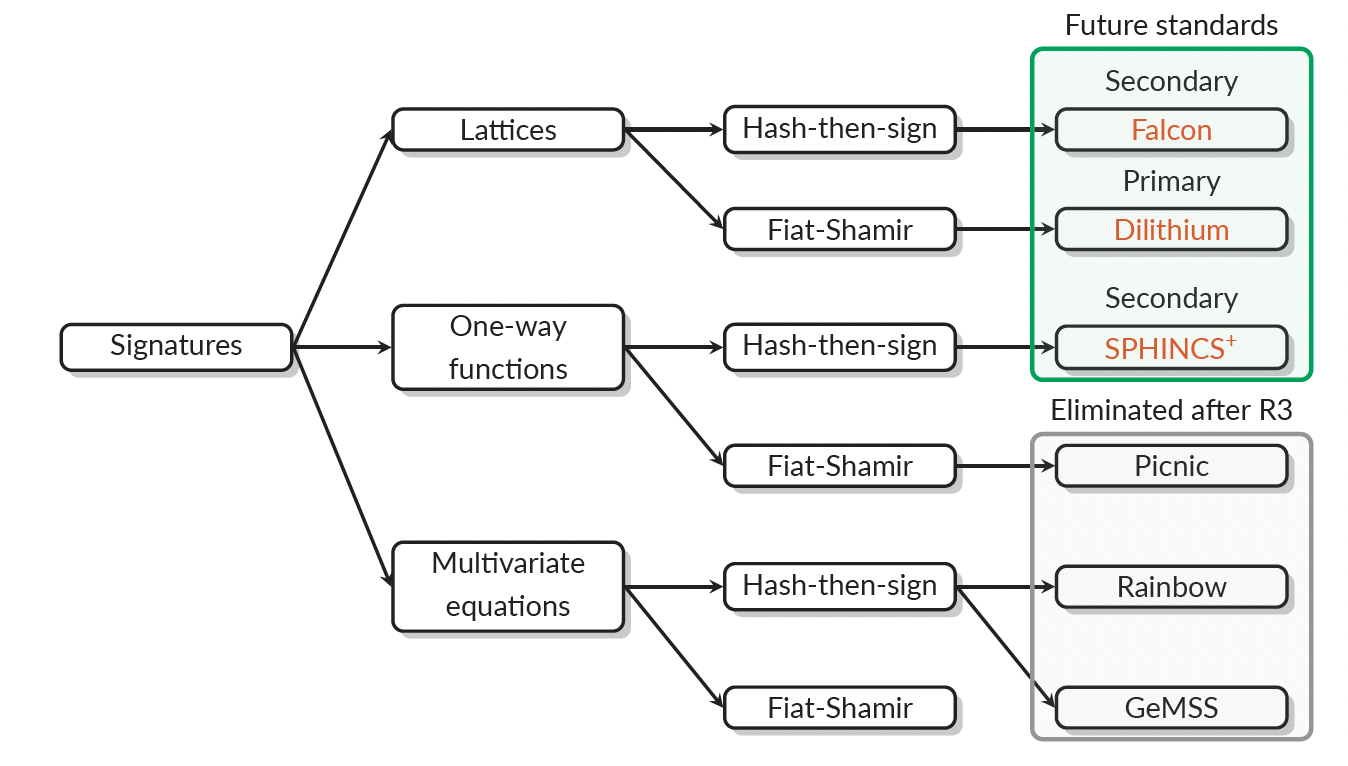
By July 2022, NIST had chosen four algorithms for inclusion in its Federal Information Processing Standard (FIPS) initiative. Among these selections, CRYSTALS-Kyber, outlined in FIPS 203, stands tailored for general encryption purposes, notably securing websites.
In tandem, CRYSTALS-Dilithium, detailed in FIPS 204, specifically addresses safeguarding digital signatures used in remote document signing. Similarly, SPHINCS+, featured in FIPS 205, serves the purpose of digital signature security. Finally, FALCON, dedicated to digital signatures, anticipates its independent draft FIPS release in 2024.
CRYSTALS-Kyber
An IND-CCA2-secure key encapsulation mechanism (KEM), whose security is based on the hardness of solving the learning-with-errors (LWE) problem over module lattices. The CRYSTALS-Kyber is a quantum-safe algorithm (QSA) and is a member of the CRYSTALS (Cryptographic Suite for Algebraic Lattices) suite of algorithms. ICSF currently supports Kyber-1024 Round 2. Kyber-1024 aims at security roughly equivalent to AES-256.
ICSF supports the CRYSTALS-Kyber Algorithm on both the PKCS #11 and CCA architectures.
PKCS #11 CRYSTALS-Kyber key operations can be performed in hardware or software.
PKCS #11 callable services that support CRYSTALS-Kyber key operations are:
PKCS #11 Derive Key (CSFPDVK and CSFPDVK6)
PKCS #11 Generate Key Pair (CSFPGKP and CSFPGKP6)
PKCS #11 Get Attribute Value (CSFPGAV and CSFPGAV6)
PKCS #11 Set Attribute Value (CSFPSAV and CSFPSAV6)
PKCS #11 Token Record Create (CSFPTRC and CSFPTRC6)
CCA callable services that support CRYSTALS-Kyber key operations are:
ECC Diffie-Hellman (CSNDEDH and CSNFEDH)
PKA Encrypt (CSNDPKE and CSNFPKE)
PKA Decrypt (CSNDPKD and CSNFPKD)
PKA Key Generate (CSNDPKG and CSNFPKG)
PKA Key Import (CSNDPKI and CSNFPKI)
PKA Key Token Build (CSNDPKB and CSNFPKB)
PKA Key Token Change (CSNDKTC and CSNFKTC)
PKA Key Translate (CSNDPKT and CSNFPKT)
PKA Public Key Extract (CSNDPKX and CSNFPKX)
Dilithium
Algorithm submitted to the NIST post-quantum cryptography project. Dilithium – digital signature scheme that is strongly secure under chosen message attacks based on the hardness of lattice problems over module lattices. The security notion means that an adversary having access to a signing oracle cannot produce a signature of a message whose signature he hasn’t yet seen, nor produce a different signature of a message that he already saw signed.
SPHINCS+
SPHINCS-256 stands as a robust post-quantum hash-based signature scheme renowned for its high-security features. On a modern 4-core 3.5GHz Intel CPU, this scheme showcases the ability to efficiently sign numerous messages per second. Notably, the signatures generated by SPHINCS-256 measure 41 KB in size, while its public and private keys are a mere 1 KB each.
Specifically crafted to withstand the potential threat posed by quantum computers, SPHINCS-256 ensures long-term security at a remarkable 2128 level, even when faced with adversaries wielding quantum capabilities. Distinguishing itself from many hash-based signature schemes, SPHINCS-256 operates in a stateless manner. This unique attribute enables it to seamlessly replace existing signature schemes without the need for complex modifications or adaptations.
Falcon
Falcon, a contender in the NIST PQC (Post-Quantum Cryptography) standard, stands alongside NTRU (Nth degree-truncated polynomial ring units) as a finalist. This cryptographic system is rooted in lattice-based methodologies, specifically designed to provide resilient digital signing in the quantum computing era. Derived from NTRU, Falcon draws upon the Gentry, Peikert, and Vaikuntanathan approach for creating lattice-based signature schemes, integrating a trapdoor sampler known as Fast Fourier sampling.
As AI and Quantum Computing continue to develop, their convergence brings both optimism and concerns. The development of countermeasures remains crucial to ensuring a secure and resilient cyber environment amidst the disruptive forces of technological innovation.










